← All Blogs

The Importance of Regular Cybersecurity Assessments
Cybersecurity is no longer a luxury but a need. With the cyber threat being an evolving beast, and at incredibly rapid rates, making sure that an organization's most sensitive data and systems are safe is of critical importance. To this end, periodic cybersecurity assessments are integral. Specially for CISO, CTO, or CEO, these assessments are no longer a checkbox for various regulations but a key strategy in protection. It’s all about regular cybersecurity assessment, whether it is vulnerability assessment, penetration testing, or risk assessment, periodic testing identifies any possible weakness way ahead of time before critical threats come in.
Beyond the immediate security advantages, it is an improvement of your organization's security stance, enhancing your reputation, and even saving money by mitigating potential breaches. However, conducting such assessments might be hampered by resources and time constraints.
The blog will include the main components, benefits, and best practices to have a strong and effective strategy in cybersecurity.
Understanding the Need for Regular Cybersecurity Assessments
The cyber threat ecosystem acts and moves as a living, breathing, ever-mutating, and evolving entity. New vulnerabilities, sophisticated attacks, and changing regulations keep security teams on their toes. Regular assessments act as your organization's early warning system, identifying potential weaknesses before they're exploited.
Beyond threat detection, assessments are the compass by which compliance ensures that you are running par for industry standards and legal requirements, ensuring brand reputation and avoiding expensive penalties.
It's not just compliance; it's risk management. Early vulnerability detection helps in prioritizing mitigation efforts and making decisions based on real information. This shields your assets from attacks, which ensures business continuity. An organization that is well-shielded in advance can fight cyber attacks that could minimize loss in terms of time and finances.
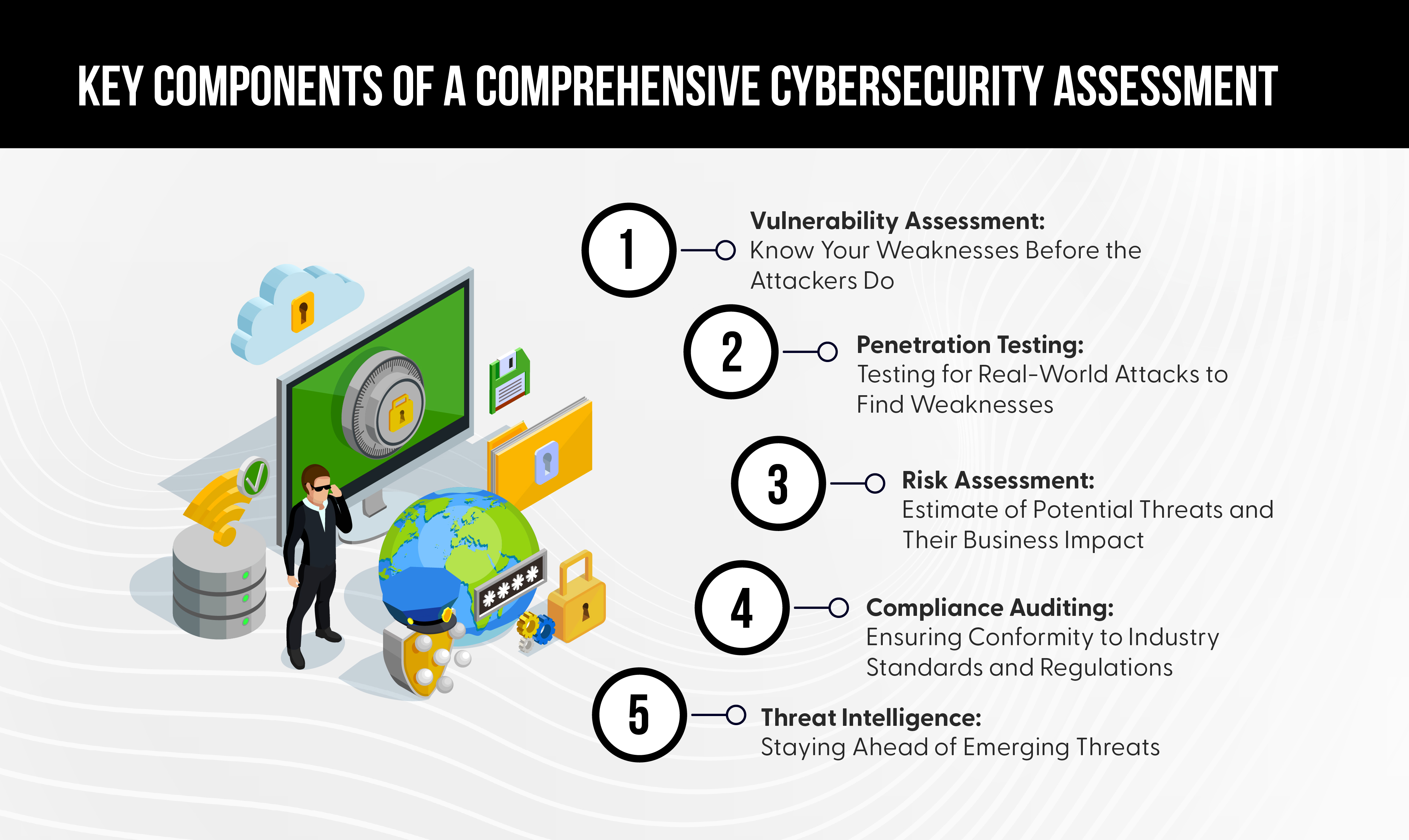
Key Components of a Comprehensive Cybersecurity Assessment
Knowing cyber threats and periodic cybersecurity assessments are not only good practice but a must in today's business environment. One such key element of these assessments provides the backbone to protect their organizations.
Let us now deliberate on the main elements that would consist of a good cybersecurity assessment.
Vulnerability Assessment:
Know Your Weaknesses Before the Attackers Do - A vulnerability assessment is a health checkup for your IT infrastructure. It makes a systemic scan of your systems, networks, and applications for weaknesses that could be targeted and turned into attack vectors by cyber criminals. Actually, statistics indicate that around 60% of data breaches in 2024 have been due to known vulnerabilities that remained unpatched.
The purpose is simple: find and fix vulnerabilities before they can be used against you. The benefit of all this? You're taking a proactive approach to security with minimal risks, especially enhancing your organization's resilience to attacks.
Penetration Testing:
Testing for Real-World Attacks to Find Weaknesses - Penetration testing, often referred to as ethical hacking, takes the concept of vulnerability assessment a step further. It involves simulating real-world attacks against your systems to find vulnerabilities that may be exploited.
Penetration testing provides insight into how a potential attacker may breach your defenses by emulating TTPs used by cybercriminals. The experience gathered will help your security team strengthen weak points and be prepared for new threats.
Risk Assessment:
Estimate of Potential Threats and Their Business Impact - The global average cost of a data breach is now $4.5 million in the year 2024, which acts as a pointer toward the financial implications that come with cyber risks. Understanding the cyber risks your organization may face underpins a sound strategy in cybersecurity.
Risk assessment is the process of identifying any potential threat—whether from internal sources, external actors, or even natural disasters—estimating its likelihood, and projecting its potential impact. Such an exercise in threat profiling aids in prioritizing security efforts so that resources are channeled toward mitigating the most critical risks. What emerges is a balanced security approach, dovetailing with the unique requirements and risk appetite of your organization.
Compliance Auditing:
Ensuring Conformity to Industry Standards and Regulations - Non-compliance is just not an option in the face of today's regulatory environment. Huge fines have been incurred due to non-compliance by some well-known companies in 2024, going as high as 4% of their global annual turnover. Compliance auditing ensures that your organization abides by industry standards and regulations like GDPR, HIPAA, or PCI-DSS.
Continuous auditing will help you not only avoid heavy fines and penalties but also prove to all your stakeholders that your organization is really taking care of security. In a nutshell, compliance in many cases involves implementing best practices that strengthen the overall security posture anyway, so it's a win-win situation.
Threat Intelligence:
Staying Ahead of Emerging Threats - Keeping your ear to the ground for emerging threats is the hallmark of security in a cybersecurity world. Threat intelligence deals with the collection, analysis, and sharing of information regarding current and potential threats that might impact your enterprise. This information will help your security team foresee and better defend against such attacks.
Adoption of AI-driven threat intelligence platforms has increased by a whopping 35% in the first quarter of 2024 alone, definitely showcasing value realized in adoption. With the integration of threat intelligence into your cybersecurity assessment, you will always stay one step ahead of any potential threats, proactively helping you respond more promptly to new threats and minimizing the window of opportunity for attackers.
Benefits of Regular Cybersecurity Assessments
Improved Security Posture: Periodic reviews of cybersecurity strengthen your defense by identifying vulnerabilities before attackers do. According to studies, 45% of organizations have seen attacks increase by 45% over the past year. For companies where regular assessments were done, there was a 30% decrease in the number of successful breaches. This will help to build a robust security framework, reduce the risk of breaches, and keep one step ahead of threats.
Cost Savings: The cost of trying not to have a cyber incident is far less than that of getting through the event. Provided assessments could be done on a regular basis, risks are mitigated at an early stage, and help in saving hundreds of dollars not only in incident response and recovery of data but also in potential regulatory fines. It is indicated that businesses that had the priority for regular assessments lowered breach-related costs by up to 50%.
Better Reputation: A strong security posture is related not only to defense but also to trust. Recent studies have shown that 72% of consumers reported they would, in fact, be more likely to trust a company with a stronger security record. Periodic assessments prove due diligence in the protection of sensitive data and will engender customer and partner trust for long-term relationships.
Competitive Advantage: Within today's marketplace, good cybersecurity represents competitive differentiation. The regular assessments prove to stakeholders that an organization stands apart from others by being serious about the protection of its most valuable assets and earning hard-won trust.
Overcoming Challenges in Implementing Regular Assessments
Resources: This is one of the most common constraints. Budget and staffing are a challenge. Be sure to consider the use of automated tools that can carry out regular assessments without extending your resources. Last but not least, third-party experts can be contracted to enhance your in-house team without long-term investment.
Time constraints: Finding time for frequent assessments can be a challenge for many in the fast-moving business environment today. Fit the assessments into your existing security protocols, making time for them. Make it easier and less time-consuming by really homing in on those major vulnerabilities and more risky areas that may need assessment, so your assessments are effective yet efficient.
Integration with business operations: It is very important to align your cybersecurity assessments in the light of your business goals. Thus, it would be best to work with business leaders in implementing measures that would actually support attaining overall objectives rather than hamper them. This not only secures your operations but also fosters a culture where cybersecurity can be seen as one of the enablers for business success and not one of the roadblocks.
Best Practices for Effective Cybersecurity Assessments
Choosing the right assessment provider: Identify vendors that have demonstrated domain expertise and deep knowledge about your industry. Look for certifications, past clients' testimonials, and a strong performance record. Make sure they have customized assessments to suit the needs of your particular situation.
Establish a strong security culture: Allow your staff to be your first line of defense. Provide regular training and open communication about the need for cybersecurity in order to foster a proactive security culture. Engage your team in the assessment process to identify and address potential gaps.
Continuous monitoring and improvement: Cybersecurity does not stop there. It is a continuous process of monitoring for the emergence of new threats and vulnerabilities. Based on assessment findings, review and update security protocols regularly to make sure that defenses against evolving risks are current.
The Future of Cybersecurity Assessments
The future of cybersecurity assessments itself is changing at a very fast pace, trying to keep up with the emerging threats. As cybercriminals get sophisticated, the tools and strategies used in the assessment should get more sophisticated. Artificial intelligence and machine learning will further strengthen threat detection and provide quicker and more accurate vulnerability assessments. This will become normal with continuous, automated testing instead of periodic checks in real time.
The more remote work becomes established, the greater the shift to cloud security and endpoint protection. Cybersecurity assessments have also put a much-needed emphasis on collaboration by drawing various teams around the complexity of the risks. Keeping ahead will require embracing these very advancements and committing to regular proactive evaluations to safeguard your organization's digital assets.
Conclusion
Regular cybersecurity assessments are essential for safeguarding your organization's sensitive data and systems. It goes beyond just compliance but is a value add of raising the security posture, saving costs, and competitive advantages.
At InterSources Inc., we are committed to helping you stay ahead of threats with our comprehensive cybersecurity services. Contact us today to strengthen your defense and ensure a robust security strategy. Your protection starts with a proactive approach.
